This is a bit of an ancient feature, but one I hadn't touched for a while. I wanted a domain cookie in my deployment, I had a Virtual Host and a standard host. host1.example.comhost2.example.com (A virtual Host). And I was struggling to get the login process (via AAC and the identifier first authentication) on the... Continue Reading →
Customize the Enroll TOTP QR Code
Sometimes you might want to put your own enrollment process into an authentication service flow. This might be for Just in time enrollment, or some other reason. I quickly prototyped this out using an infomap, and just want to put it here for reference later. In short, it uses the easy native functions to detect... Continue Reading →
IBM Security Verify Access – Better defaults
IBM Security Verify Access (ISVA) (formerly IBM Security Access Manager - ISAM) has been around for a fair while, and has made a series of assumptions over it's time, starting fresh, you might not make those assumptions if you were deploying ISVA today. Upgrades for existing customers rarely bring onboard these changes to avoid backwards... Continue Reading →
Custom SMS/Email OTPs messages per brand
Branded SMS and Email OTP messages with IBM Security Verify Access just takes a few steps with IBM Security Verify Access. First thing you need to do - is determine how you plan to differentiate the inbound request from a different brand. In this example, we'll do it based on an inbound HTTP header to... Continue Reading →
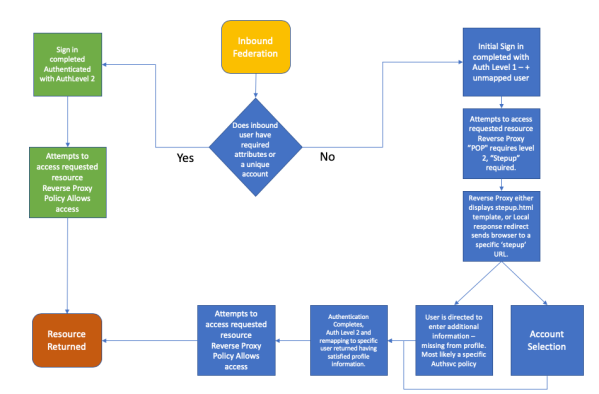
Partial Authentication on inbound federation
How do you handle a partially authenticated state when the inbound user is either missing attributes, or needs to select from multiple mapped accounts when accessing resources protected by ISAM or what is now IBM Security Verify Access.
Using ISAM with a Single Page Application (SPA)
Over on the ISAM blog on ibm.com, I've just completed an indepth article on using ISAM with a Single Paged Application. These are typically applications that use JavaScript, AJAX, Angular and other frameworks to make a very dynamic user experience on a website. Think of any site you've used where the whole page doesn't reload... Continue Reading →
Build an ISAM developer Portal for OAuth Grants
My friend Leo has just posted details on how to make use of the OAuth provisioning APIs exposed via Infomap, you can take a look at the details here: https://www.ibm.com/blogs/security-identity-access/2018/06/oauth-building-developer-portal/ This is one of the best things you can do to enable your ISAM infrastructure to be easily consumed by your organizations developers. They can... Continue Reading →
ISAM OAuth Inactivity
Its not immediately obvious, and commonly misconstrued as an problem of disappearing tokens, but the OAuth grants in ISAM have a "Maximum" Grant lifetime, as opposed to an inactivity in a default API Definition. This means that when you request a Token - say via ROPC and you are using the default settings of an... Continue Reading →
ISAM Facebook Login with OIDC Relying Party
In ISAM 9.0.4.0 the OIDC relying party was completely rewritten for increased flexibility. This has made it much easier to add support for Facebook Login into an ISAM Reverse Proxy instance. Here are the steps I've taken to authenticate into ISAM with Facebook. Pre-Conditions: ISAM 9.0.4.0 - Preconfigured Standard WebSEAL reverse Proxy with default configuration.... Continue Reading →
Simpler ISAM Authentication Service URLs
This article is no longer necessary, thanks to OOTB behavior available in ISAM 9.0.6 and later. See details here. In order to clean up the instantiation URLs generated by the authentication service, you can use a ISAM HTTP transformation rule. I've just completed two examples of this. Remove PolicyId static prefix: No static Prefix This... Continue Reading →
ISAM – Redirect on Logout or show login page on logout
A simple post here - a quick guide on how you redirect to a specific url after logging out. In the ISAM reverse proxy, you can make use of the operation based Local Response Redirect, to send you to a specific location once you have logged out. To enable this, enable local response redirect, #--------------------------... Continue Reading →
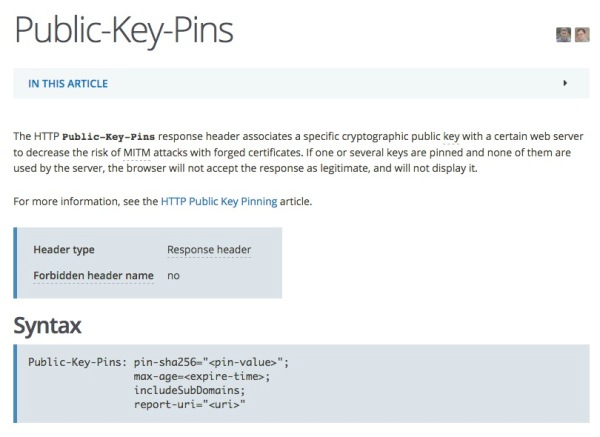
HTTP Public Key Pinning Header with ISAM and WebSEAL
HTTP Public Key Pinning is a header that allows you to pin a certificate to a host, consider it the next step after HSTS ISAM for Web & Sending Security HTTP Headers the solution isn't any different to send the header with WebSEAL. The HTTP Public-Key-Pins response header associates a specific cryptographic public key with... Continue Reading →
ISAM – Infomap – Any alias authentication
A number of customers like to use various alias's to authenticate into ISAM, up until recently, the primary way of achieving this, is via a Custom EAI, or some elaborate LDAP hackery. Infomap, and the UserHelper capabilities, makes this a much easier affair. Here is an example, where we use the infomap to authenticate based... Continue Reading →
ISAM JavaScript – Making Multi value Attributes
Received a question related to the 'art' of making an attribute that is multivalued for the purpose of a SAML Mapping rule, but this is still relevant when using Infomap, OAuth or even the AuthSvcCred mapping rules. When we are writing the JavaScript mapping rules, the engine wants to make JavaScript objects, this is useful... Continue Reading →
ISAM create a new OTP Mechanism
I wanted to make a new OTP Mechanism that was called by a JavaScript REST call - that wasn't the SMS mechanism in the box. In this example - I tested it with Boxcar - an iOS App that lets you send Push notifications with a simple REST call. To add a custom mechanism to... Continue Reading →