When trying to configure an EAI, I encountered the following error whenever it was supposed to be authenticating the user: Server Error Access Manager WebSEAL could not complete your request due to an unexpected error. Diagnostic Information Method: GET URL: <url> Error Code: 0x38cf042f Error Text: Server Error Solution Provide your System Administrator with the... Continue Reading →
ISAM Error: HPDBA0222E
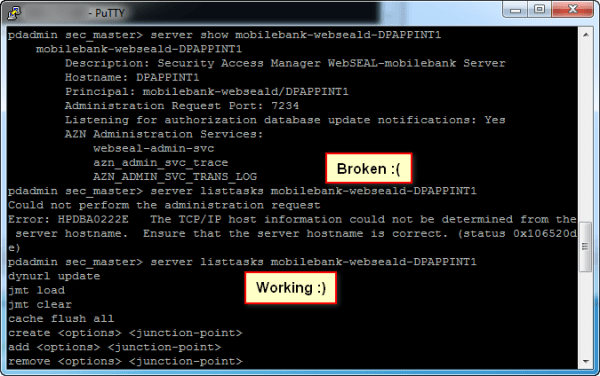
I started experimenting with ISAM for DataPower today, and in doing so, encountered a fun bug based on my environment. When creating a Junction, nothing appeared to happen. Eventually in attempting to debug using pdadmin on the DP Commandline interface, I ran the command: pdadmin sec_master> server listtasks mobilebank-webseald-DPAPPINT1 Could not perform the administration request... Continue Reading →
ISAM Appliance Networking Changes
In ISAM v8.0.1.2, some fairly significant changes were introduced to the Management of the ISAM appliance networking interfaces. The update removed the concept of separate NICs for Application and Management interfaces and instead bound those concepts to an IP Address. It added support for VLAN tagging on packets, and provides a number of enhancements around... Continue Reading →
Determine ISAM Appliance MAC Address
It can be a little confusing to get the MAC Address of the ISAM appliance network interfaces, which is particularly useful in virtualised environments. I've been in circumstances where you want to add/remove networking interfaces, but the order in which they are described in VMWare rarely corresponds to the order they are assigned when the... Continue Reading →
OAuth Authorization
When using ISAM in OAuth patterns, there are a number of ways you can do authorization based on OAuth scopes. In general, at last check, there are three main ways of Authorizing OAuth requests based on their scope. (or other attributes associated with the tokens). The mechanisms available are dependent on which OAuth validation mechanism... Continue Reading →
ISAM Authorization Rule for OAuth Scope
The vast majority of the work in developing this Authorization Rule was developed by my colleague Shane Weeden. Thanks for sharing Shane! Find more of his work here: https://www-304.ibm.com/connections/blogs/sweeden/?lang=en_us This authorization rule extracts the OAuth values of scope from the ISAM credential and applies a TRUE or FALSE authorization result subject to it containing the... Continue Reading →
ISAM Context Based Access PIP for OAuth
The vast majority of the work in developing this PIP was done by my colleague Scott Andrews. Thanks for sharing Scott! Find more of his work here: https://ibm.biz/securityintegration Building from the example PIP in my article here: ISAM JavaScript Policy Information Points here is a PIP that extracts the OAuth values of scope and supplies... Continue Reading →
SSO from Native Mobile application to Browser
I'm in the process of formalising an integration with ISAM for Web and ISAM for Mobile where we provide SSO from a Native mobile application into the mobile browser. If this is something you're interested in, please get in contact with me. I'm keen to hear your requirements. This pattern is particularly useful since... Continue Reading →
ISAM for Web – Different login pages per junction
Update 15/05/2015: It would seem that I may have over complicated this, we have a ISAM feature to do this already! 🙂 Apparently since TAM 6.1.1 we can use static management and error page templates per junction, as stated in the following technote: http://www-01.ibm.com/support/docview.wss?uid=swg21587936 So feel free to choose your own adventure! Different people access... Continue Reading →
ISAM for Web – Clickjacking prevention
What is Clickjacking? Clickjacking (User Interface redress attack, UI redress attack, UI redressing) is a malicious technique of tricking a Web user into clicking on something different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages. It... Continue Reading →
ISAM for Web – Sending Security HTTP Headers
Update 5/08/15: In the ISAM 8.0.1.3 Release, we've added a new stanza to the ISAM Reverse Proxy config file. This allows the easy addition of headers to all ISAM responses. [rsp-header-names] # # This stanza is used to define static HTTP headers which will be added # to every HTTP response from the WebSEAL server. ... Continue Reading →
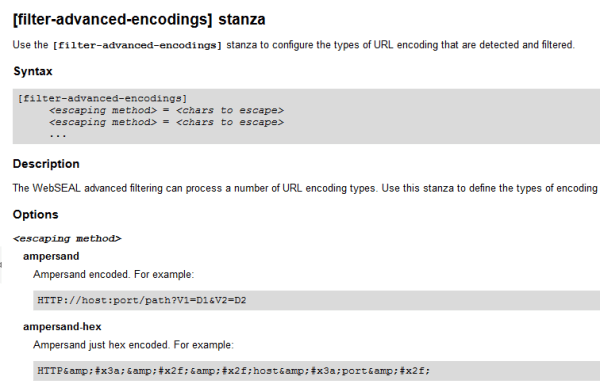
Encoded URLs and WebSEAL filtering
If you have encoded URLs in scripting thats protected by WebSEAL, it won't automatically filter it, unless you configure the encoding. For example: Javascript Link Backslash U hex encoded: var a = document.createElement('a'); var label = "http:u002fu002fsomeserver:8080u002fdemou002fblah"; a.href = label; var linkText = document.createTextNode(label); a.appendChild(linkText); a.title = "my title text"; a.href = label; document.body.appendChild(a); Without... Continue Reading →
ISAM – POODLE updates
When I attempted to configured ISAM for Mobile V8.0.1.0 against an old version of TAM - specifically TAM Policy Server v 6.1.1 FP 8 (and an older 6.1.1 - FP4), I ran into some problems. It generated the following error: System Error HPDCF0062E Could not connect to the Security Access Manager policy server. Error code... Continue Reading →
ISAM for Web – Modify a Request Header
I posted about modifying a HTTP response back in June 2014 here. This month, I had to put together a HTTP transformation rule that would update a Request header. In particular, the Request header was "out of spec" from the HTTP rules for a Content-Type. It simply updated the request header. <?xml version="1.0" encoding="UTF-8"?> <xsl:stylesheet... Continue Reading →
ISAM for Web without a User Registry – New and Improved
In 2009, Shane Weeden posted an article about using WebSEAL without a user registry. The article made use of a number of components, including TFIM as a mechanism to generate an ISAM credential and return that to WebSEAL to build a session. This pattern is particularly useful in scenarios where the users are stored in... Continue Reading →