In ISAM using the Local Response Redirect capability has traditionally been overkill when using it for an EAI for a login operation. The reason being, almost any error or management page that is traditionally handled by ISAM now gets redirected to your EAI. Including Login operations, Logout page, Stepup and other authentication related operations. It... Continue Reading →
OAuth Auth ISAM authentication level mapping
ISAM provides the concept of Authentication Levels out of the box. This means a given authentication mechanism or flow can be assigned an integer value >0 that represents the authentication strength. OAuth Auth can make use of this for features such as incremental authentication - for example if the OAuth grant was issued via single... Continue Reading →
Setting an Authentication Level for Kerberos in ISAM
Tying an authentication mechanism to an authentication level can be very useful when writing security policy in ISAM. For example you might want a password based authentication (Such as Basic Auth or Forms Auth) to map to level 1, whilst you might hold a federated identity, or something achieved through another EAI to have a... Continue Reading →
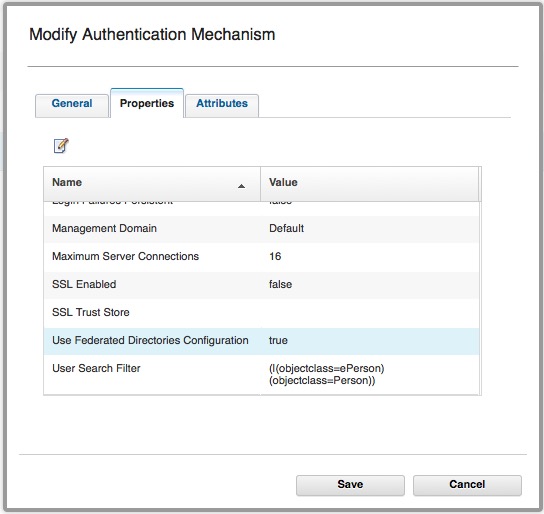
Using Basic Users with OAuth-Auth and ROPC
It is possible to use Basic Users with the ISAM OAuth-Auth capabilities. (ISAM Basic users are users that have NOT been imported into the ISAM registry.) Authentication used to be performed by: isAuthenticated = PluginUtils.isValidUsernamePassword(username, password); I've talked about how this is configured here. This authentication mechanism *can* be configured to use Federated Registries, however... Continue Reading →
Advanced ISAM Session Timeout capabilities
Sometimes it might be necessary to manage a session lifetime based on business or security factors, and these might need to be specific to an operation in progress. Here are some helpful techniques for managing the timeouts more dynamically: Understanding Session timeout accuracy Before we go into more detail of setting the session timeouts - it's... Continue Reading →
ISAM LMI REST API – HTTP 405 Method not Allowed Error
When using the REST API to run some commands against an ISAM for Web/Mobile Appliance, I ran into an HTTP error code that wasn't immediately obvious. Status Code: 405 Method Not Allowed There was no issue with the POST Method, but rather the headers that I sent. It's vitally important that you send the "Accept"... Continue Reading →
IBM Security Access Manager (ISAM) Kerberos Configuration Guide
My colleague has posted an in depth set of articles on IBM DeveloperWorks for Kerberos configuration with ISAM. It covers both Kerberos integration's, being Desktop SSO with Kerberos into ISAM, and junctioning to servers using Kerberos for Junction SSO. The article is available here: https://www.ibm.com/developerworks/community/wikis/home?lang=en#!/wiki/W746177d414b9_4c5f_9095_5b8657ff8e9d/page/Information%20and%20Guides%20for%20Kerberos%20SSO
ISAM Forms SSO into BMC Remedy
Updated 09/2015: HTTP 505 error solved. See end of article. On a customer site, I encountered BMC Remedy, and had to perform SSO into the Application from ISAM. My initial attempt included trying to use the standard integration we have with Tomcat versions, as detailed here: http://www-01.ibm.com/support/docview.wss?uid=swg24021393 Unfortunately, this didn't work in the time I'd... Continue Reading →
ISAM EAI Server Error: 0x38cf042f
When trying to configure an EAI, I encountered the following error whenever it was supposed to be authenticating the user: Server Error Access Manager WebSEAL could not complete your request due to an unexpected error. Diagnostic Information Method: GET URL: <url> Error Code: 0x38cf042f Error Text: Server Error Solution Provide your System Administrator with the... Continue Reading →
ISAM Appliance Networking Changes
In ISAM v8.0.1.2, some fairly significant changes were introduced to the Management of the ISAM appliance networking interfaces. The update removed the concept of separate NICs for Application and Management interfaces and instead bound those concepts to an IP Address. It added support for VLAN tagging on packets, and provides a number of enhancements around... Continue Reading →
OAuth Authorization
When using ISAM in OAuth patterns, there are a number of ways you can do authorization based on OAuth scopes. In general, at last check, there are three main ways of Authorizing OAuth requests based on their scope. (or other attributes associated with the tokens). The mechanisms available are dependent on which OAuth validation mechanism... Continue Reading →
ISAM Authorization Rule for OAuth Scope
The vast majority of the work in developing this Authorization Rule was developed by my colleague Shane Weeden. Thanks for sharing Shane! Find more of his work here: https://www-304.ibm.com/connections/blogs/sweeden/?lang=en_us This authorization rule extracts the OAuth values of scope from the ISAM credential and applies a TRUE or FALSE authorization result subject to it containing the... Continue Reading →
ISAM for Web – Different login pages per junction
Update 15/05/2015: It would seem that I may have over complicated this, we have a ISAM feature to do this already! 🙂 Apparently since TAM 6.1.1 we can use static management and error page templates per junction, as stated in the following technote: http://www-01.ibm.com/support/docview.wss?uid=swg21587936 So feel free to choose your own adventure! Different people access... Continue Reading →
ISAM for Web – Clickjacking prevention
What is Clickjacking? Clickjacking (User Interface redress attack, UI redress attack, UI redressing) is a malicious technique of tricking a Web user into clicking on something different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages. It... Continue Reading →
ISAM for Web – Sending Security HTTP Headers
Update 5/08/15: In the ISAM 8.0.1.3 Release, we've added a new stanza to the ISAM Reverse Proxy config file. This allows the easy addition of headers to all ISAM responses. [rsp-header-names] # # This stanza is used to define static HTTP headers which will be added # to every HTTP response from the WebSEAL server. ... Continue Reading →