Sometimes its necessary to quickly setup a demo host with IBM Security Verify Access (ISVA) and you need something that will output some diagnostic information. Introducing the https://resource-server-demo.verify.ibm.com/ This is an IBM Hosted demo host - that gives you some demo resources - so you can try out ACLs, or more elaborate configuration. Setting it... Continue Reading →
Compress Log Files and Audit Logs on Reverse Proxy
A simple but useful feature, is the ability in IBM Security Verify Access to compress rolled over files generated by the Reverse Proxy. This includes the audit logs, request logs, referrer logs etc. By default, the rolled over files are plain text, but this can add up - if you intend to store them for... Continue Reading →
Domain Cookies and the Reverse Proxy
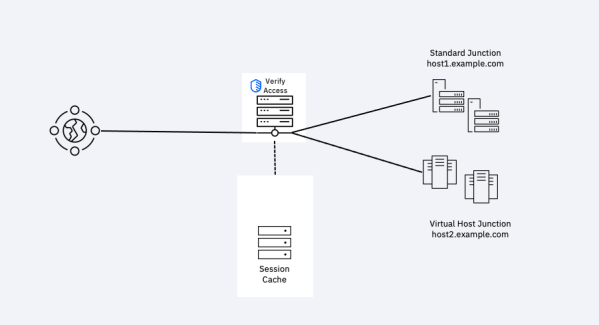
This is a bit of an ancient feature, but one I hadn't touched for a while. I wanted a domain cookie in my deployment, I had a Virtual Host and a standard host. host1.example.comhost2.example.com (A virtual Host). And I was struggling to get the login process (via AAC and the identifier first authentication) on the... Continue Reading →
Customize the Enroll TOTP QR Code
Note: This has been superseded - with new OTP enrollement experience in v10.0.8. Where there is now a native enrollment mechanism. But the inline Authsvc callout from infomap might still be useful as an example. Sometimes you might want to put your own enrollment process into an authentication service flow. This might be for Just... Continue Reading →
IBM Security Verify Access – Better defaults
IBM Security Verify Access (ISVA) (formerly IBM Security Access Manager - ISAM) has been around for a fair while, and has made a series of assumptions over it's time, starting fresh, you might not make those assumptions if you were deploying ISVA today. Upgrades for existing customers rarely bring onboard these changes to avoid backwards... Continue Reading →
Custom SMS/Email OTPs messages per brand
Branded SMS and Email OTP messages with IBM Security Verify Access just takes a few steps with IBM Security Verify Access. First thing you need to do - is determine how you plan to differentiate the inbound request from a different brand. In this example, we'll do it based on an inbound HTTP header to... Continue Reading →
Partial Authentication on inbound federation
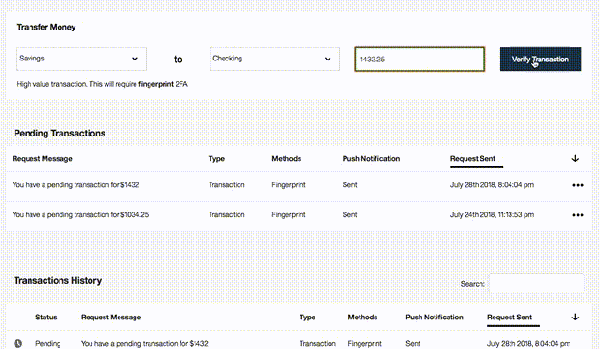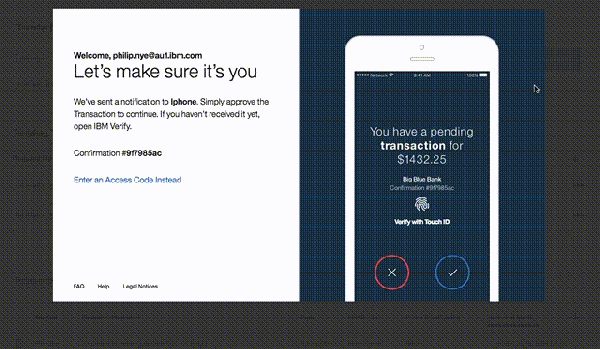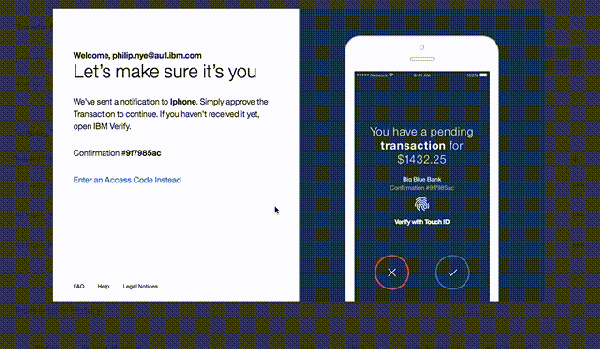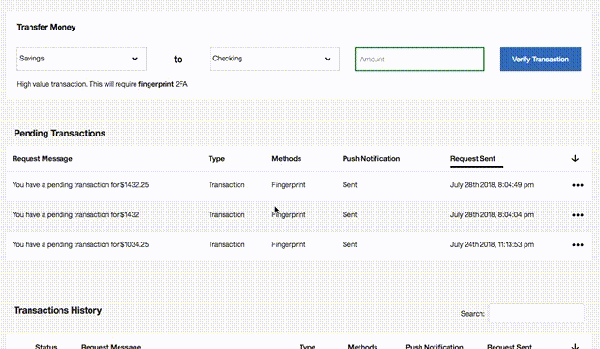
How do you handle a partially authenticated state when the inbound user is either missing attributes, or needs to select from multiple mapped accounts when accessing resources protected by ISAM or what is now IBM Security Verify Access.
Using ISAM with a Single Page Application (SPA)
Over on the ISAM blog on ibm.com, I've just completed an indepth article on using ISAM with a Single Paged Application. These are typically applications that use JavaScript, AJAX, Angular and other frameworks to make a very dynamic user experience on a website. Think of any site you've used where the whole page doesn't reload... Continue Reading →