NOTE: The Keystash has been enhanced, and is no longer accessible this way. If you've lost your keystore password now - all bets are off. Sorry. On the other hand, if you at least have the stash, you can likely export the keys and move them into a new keystore of your choice, with a... Continue Reading →
TFIM SAML 2.0 Federation URL
Sample Federation URL: I make this post, as much about a note to myself - as for others. This URL will avoid using the Alias service, and initiate a HTTPPost SAML flow. https://<idpHost>/FIM/sps/<federationname>/saml20/logininitial?RequestBinding=HTTPPost&ResponseBinding=HTTPPost&NameIdFormat=Email&PartnerId=<ID for partner> Here is some additional notes from the IBM Knowledge Center: http://www-01.ibm.com/support/knowledgecenter/SSZSXU_6.2.2.6/com.ibm.tivoli.fim.doc_6226/admin/concept/handlingunspecifiednameid.html
ISAM for Mobile: Javascript Policy Information Points
Since 8.0.0.3 ISAM for Mobile has had the ability to call a Javascript Policy Information Point (PIP) during context based access (CBA, formerly risk based access - RBA) decisions for attribute enrichment. This capability is very flexible and can be used for many different purposes. Some examples include: Manipulating and extracting attributes from request headers.... Continue Reading →
ISAM for Web – WebSEAL – Firefox doesn’t ask for client certificate
Just spent a while troubleshooting why my browser wouldn't ask me for the client certificate even when I went to a certificate protected webseal instance. After a while, I worked it out, and thought I'd make a note of it here. Title Note: It was actually happening on both Firefox AND Internet Explorer. Pre-conditions: forms-auth... Continue Reading →
ISAM for Web – WebSEAL – Stream EAI authentication response to browser
By default, when External Authentication Interface (EAI) authentication has been configured, and the authentication header is returned to WebSEAL by the backend application server, WebSEAL authenticates the user, and then generates a 302 redirect to either the cached request or the login redirect url. If you want the page returned to the browser but the... Continue Reading →
ISAM for Web – WebSEAL Certificate Mapping
Since the move to the ISAM for Web Appliance, certificate mapping for client authentication is performed by an XSL stylesheet mapping mechanism. Since it was not immediately obvious to me, I've included two examples here where the CN of the certificate, is used as the username for the user in ISAM. Provide Full LDAP DN:... Continue Reading →
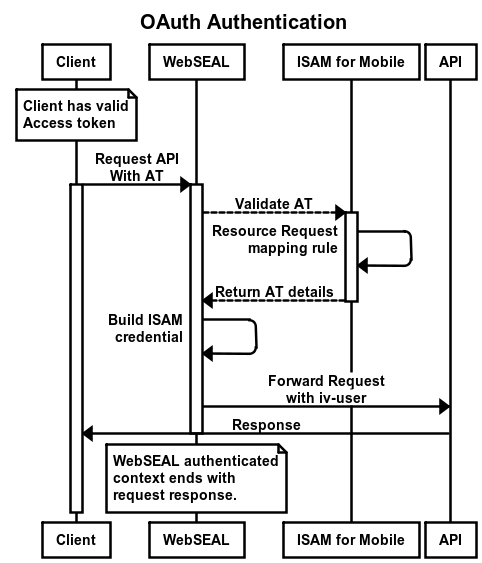
ISAM for Web and Mobile – OAuth Authentication and Sessions
[14 July, 2016] There has been a few updates to this article related to the ISAM 9.0.1 release, adding some enhancements for OAuth. This includes enhancements to the session lifetime, and session logout, also some technical updates regarding the use of DSC. 13 Jan, 20201 (Actually well before this) There was a change the DSC... Continue Reading →
Remove a ISAM for Web Response Header
If you want to hide a header from a junctioned server, it is possible to remove it using a HTTP Transformation rule. The steps to making a HTTP Transformation rule are fairly well documented here: http://www-01.ibm.com/support/knowledgecenter/SSPREK_8.0.0.4/com.ibm.isamw.doc_8.0.0.4/wrp_config/concept/con_http_transforms.html?lang=en On the appliance, you need to either create the XSL HTTP Transformation rule and upload it, or you can... Continue Reading →
ISAM for Mobile: Trace statements in Mapping Rules
Edit (13/1/15): There is another example of trace statements which references a different class in the article: ISAM for Mobile: Javascript Policy Information Points Debugging IBM Security Access Manager (ISAM) for Mobile Mapping rules can be challenging. One of the things that makes it much easier is having regular trace statements. In developing the... Continue Reading →
ISAM for Mobile: Accessing HTTP Headers in Authentication Service Mapping Rules
On the IBM Security Access Manager (ISAM) for Mobile appliance, the authentication service exposes a number of mapping rules. Four of them are related to the OTP capabilities and the last one is a mapping rule that fires once the authentication service has completed and allows manipulation of the returned ISAM credential. I have a... Continue Reading →
ISAM for Mobile: OAuth Authorization in Mapping Rules
If you'd like to do Authorization in a mapping rule for OAuth, there are a couple of options as to how you do this. On the IBM Security Access Manager (ISAM) for Mobile appliance, API protection exposes two Mapping rules: A) A Pre Token Generation mapping rule named: <API Definition Name>PreTokenGeneration. This mapping rule fires... Continue Reading →
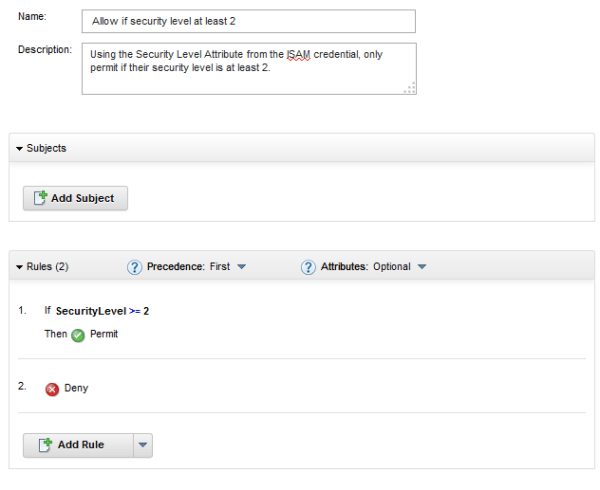
IBM Security Access Manager: Protecting your site with Context Based Access
In January, I published an article through developerWorks on protecting your website with some of the new features of the ISAM for Web and ISAM for Mobile appliances. It's available here: http://www.ibm.com/developerworks/mobile/library/se-accessmanager/index.html It makes use of Virtual Host Junctions, WebSEAL authentication levels and the comprehensive context based access engine and one time password capabilities in... Continue Reading →