When using ISAM in OAuth patterns, there are a number of ways you can do authorization based on OAuth scopes. In general, at last check, there are three main ways of Authorizing OAuth requests based on their scope. (or other attributes associated with the tokens). The mechanisms available are dependent on which OAuth validation mechanism... Continue Reading →
ISAM Authorization Rule for OAuth Scope
The vast majority of the work in developing this Authorization Rule was developed by my colleague Shane Weeden. Thanks for sharing Shane! Find more of his work here: https://www-304.ibm.com/connections/blogs/sweeden/?lang=en_us This authorization rule extracts the OAuth values of scope from the ISAM credential and applies a TRUE or FALSE authorization result subject to it containing the... Continue Reading →
ISAM Context Based Access PIP for OAuth
The vast majority of the work in developing this PIP was done by my colleague Scott Andrews. Thanks for sharing Scott! Find more of his work here: https://ibm.biz/securityintegration Building from the example PIP in my article here: ISAM JavaScript Policy Information Points here is a PIP that extracts the OAuth values of scope and supplies... Continue Reading →
ISAM for Web – Different login pages per junction
Update 15/05/2015: It would seem that I may have over complicated this, we have a ISAM feature to do this already! 🙂 Apparently since TAM 6.1.1 we can use static management and error page templates per junction, as stated in the following technote: http://www-01.ibm.com/support/docview.wss?uid=swg21587936 So feel free to choose your own adventure! Different people access... Continue Reading →
ISAM for Web – Clickjacking prevention
What is Clickjacking? Clickjacking (User Interface redress attack, UI redress attack, UI redressing) is a malicious technique of tricking a Web user into clicking on something different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages. It... Continue Reading →
ISAM for Web – Sending Security HTTP Headers
Update 5/08/15: In the ISAM 8.0.1.3 Release, we've added a new stanza to the ISAM Reverse Proxy config file. This allows the easy addition of headers to all ISAM responses. [rsp-header-names] # # This stanza is used to define static HTTP headers which will be added # to every HTTP response from the WebSEAL server. ... Continue Reading →
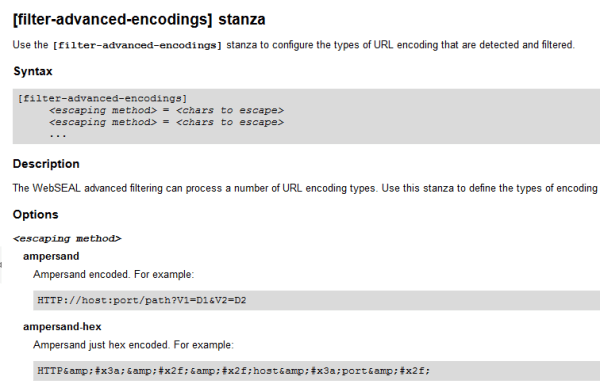
Encoded URLs and WebSEAL filtering
If you have encoded URLs in scripting thats protected by WebSEAL, it won't automatically filter it, unless you configure the encoding. For example: Javascript Link Backslash U hex encoded: var a = document.createElement('a'); var label = "http:u002fu002fsomeserver:8080u002fdemou002fblah"; a.href = label; var linkText = document.createTextNode(label); a.appendChild(linkText); a.title = "my title text"; a.href = label; document.body.appendChild(a); Without... Continue Reading →
ISAM – POODLE updates
When I attempted to configured ISAM for Mobile V8.0.1.0 against an old version of TAM - specifically TAM Policy Server v 6.1.1 FP 8 (and an older 6.1.1 - FP4), I ran into some problems. It generated the following error: System Error HPDCF0062E Could not connect to the Security Access Manager policy server. Error code... Continue Reading →
ISAM for Web – WebSEAL – Stream EAI authentication response to browser
By default, when External Authentication Interface (EAI) authentication has been configured, and the authentication header is returned to WebSEAL by the backend application server, WebSEAL authenticates the user, and then generates a 302 redirect to either the cached request or the login redirect url. If you want the page returned to the browser but the... Continue Reading →
IBM Security Access Manager: Protecting your site with Context Based Access
In January, I published an article through developerWorks on protecting your website with some of the new features of the ISAM for Web and ISAM for Mobile appliances. It's available here: http://www.ibm.com/developerworks/mobile/library/se-accessmanager/index.html It makes use of Virtual Host Junctions, WebSEAL authentication levels and the comprehensive context based access engine and one time password capabilities in... Continue Reading →
Biggest Data Breaches
Stumbled across this infographic of the major data breaches of the last decade... Over the past decade, the size and complexity of attacks has been increasing, what I find of most concern in this diagram is not only the fact that many of them are described as 'unknown' which is a combination of companies not... Continue Reading →