The vast majority of the work in developing this PIP was done by my colleague Scott Andrews. Thanks for sharing Scott! Find more of his work here: https://ibm.biz/securityintegration Building from the example PIP in my article here: ISAM JavaScript Policy Information Points here is a PIP that extracts the OAuth values of scope and supplies... Continue Reading →
SSO from Native Mobile application to Browser
I'm in the process of formalising an integration with ISAM for Web and ISAM for Mobile where we provide SSO from a Native mobile application into the mobile browser. If this is something you're interested in, please get in contact with me. I'm keen to hear your requirements. This pattern is particularly useful since... Continue Reading →
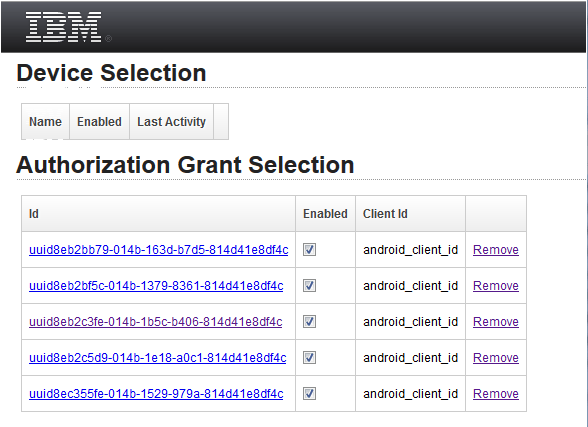
Cannot delete OAUTH grants and devices on ISAM for Mobile
When using ISAM for Mobile, and you access the User Self Service/User Self Care pages for managing OAuth Grants, there is the option to delete and manage your grants. https://<ISAM for Mobile Host>/mga/sps/mga/user/mgmt/html/device/device_selection.html In earlier versions of ISAM for Mobile, the configuration prevented DELETE and PUT operations. This meant that WebSEAL would not allow the... Continue Reading →
ISAM for Mobile – ROPC OAuth Username and Password Validation
As of V8.0.1.0 of ISAM for Mobile, there is a helper class in the Javascript mapping rule for Resource Owner Password Validation against the configured LDAP server. There are a few steps required to configure it though. If you haven't configured it, you will receive the following error on attempting an ROPC flow: {"error":"mapping_error", "error_description":"com.tivoli.am.rba.exception.RBARuntimeException:... Continue Reading →
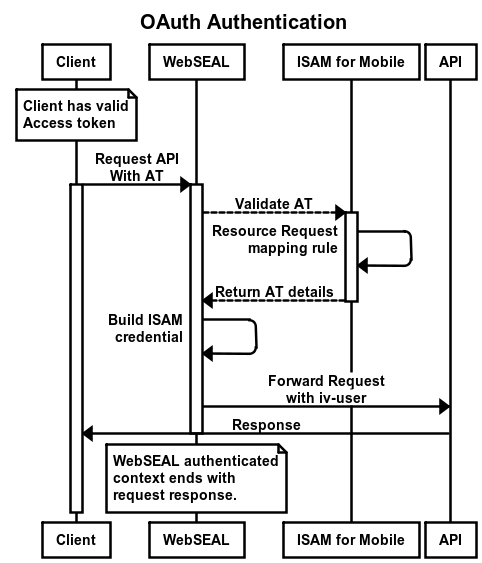
ISAM for Web and Mobile – OAuth Authentication and Sessions
[14 July, 2016] There has been a few updates to this article related to the ISAM 9.0.1 release, adding some enhancements for OAuth. This includes enhancements to the session lifetime, and session logout, also some technical updates regarding the use of DSC. 13 Jan, 20201 (Actually well before this) There was a change the DSC... Continue Reading →
ISAM for Mobile: Trace statements in Mapping Rules
Edit (13/1/15): There is another example of trace statements which references a different class in the article: ISAM for Mobile: Javascript Policy Information Points Debugging IBM Security Access Manager (ISAM) for Mobile Mapping rules can be challenging. One of the things that makes it much easier is having regular trace statements. In developing the... Continue Reading →
ISAM for Mobile: OAuth Authorization in Mapping Rules
If you'd like to do Authorization in a mapping rule for OAuth, there are a couple of options as to how you do this. On the IBM Security Access Manager (ISAM) for Mobile appliance, API protection exposes two Mapping rules: A) A Pre Token Generation mapping rule named: <API Definition Name>PreTokenGeneration. This mapping rule fires... Continue Reading →